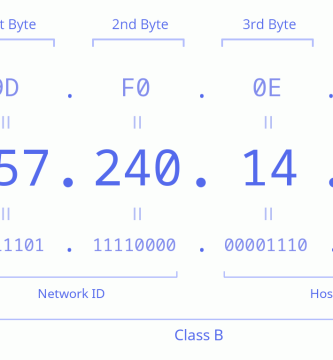
18 octubre, 2020

5 consejos para mantener tu laptop segura
11 junio, 2020

¿Qué es un servidor Proxy y para qué sirve?
3 febrero, 2020

¿Qué es y para qué sirve Wireshark?
28 febrero, 2019

Robo de Identidad: ¿Qué significa y como me afectaría?
19 octubre, 2018

¿Qué es y para qué sirve un Firewall?
12 octubre, 2018

¿Qué es y para qué sirve un certificado de seguridad SSL?
5 septiembre, 2018

El instalador de Fortnite tiene un serio defecto de seguridad
3 septiembre, 2018

Cómo borrar correo electrónico en Gmail luego de enviarlo
30 agosto, 2018
Google confirma que hace seguimiento de tu ubicación sin permiso
30 agosto, 2018

Cómo prevenir el phishing empresarial
29 agosto, 2018

Las organizaciones aún tienen problemas con la administración básica de firewall
24 agosto, 2018

Organizaciones luchan con los principios básicos del ciberhigiene
23 agosto, 2018

Fortnite para Android pondrá en riesgo seguridad de jugadores
16 agosto, 2018

Nuevo tipo de ciberataque capta datos bancarios a través de enrutadores
14 agosto, 2018

Avast retira CCleaner 5.45 tras controversia de privacidad
10 agosto, 2018

Malwarebytes lanza una nueva extensión de navegador para Chrome y Firefox
9 agosto, 2018