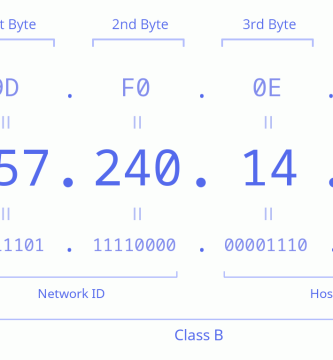
15 enero, 2023

¿Cómo proteger mi identidad digital?
3 enero, 2023

¿Puede tu ISP saber lo que haces en internet?
18 octubre, 2020

5 consejos para mantener tu laptop segura
11 junio, 2020

¿Qué es un servidor Proxy y para qué sirve?
25 marzo, 2020

¿Qué es y para qué sirve Burp Suite?
3 febrero, 2020

¿Qué es y para qué sirve Wireshark?
25 septiembre, 2019
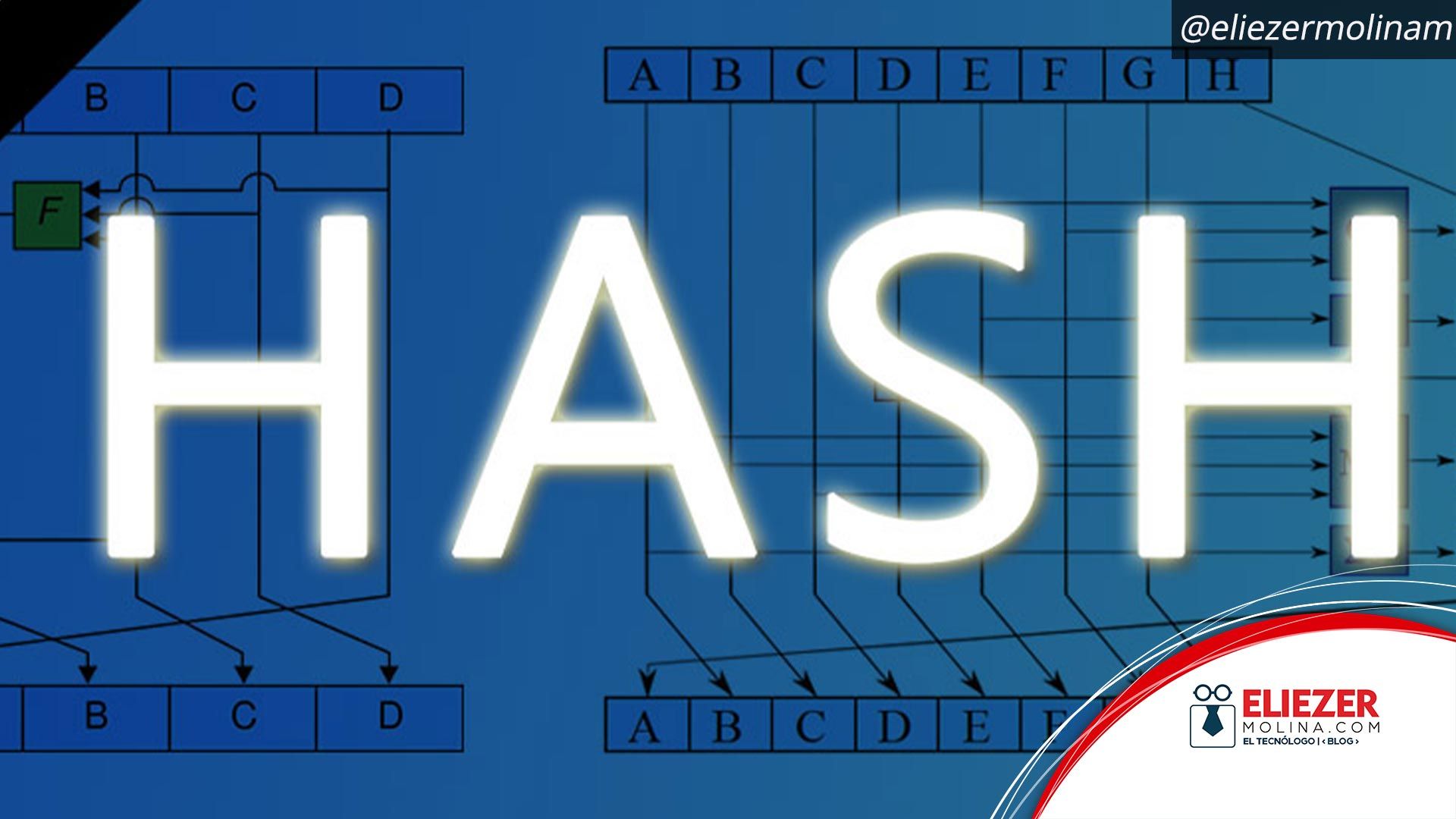
¿Qué es y para qué sirve el código HASH?
21 mayo, 2019

¿Qué es y para qué sirve BitTorrent?
13 mayo, 2019

¿Cómo funcionan las redes P2P o Torrent?
19 abril, 2019

¿Qué son y para qué sirven los test online?
15 abril, 2019

¿Qué es y para qué sirve Docker?
12 marzo, 2019
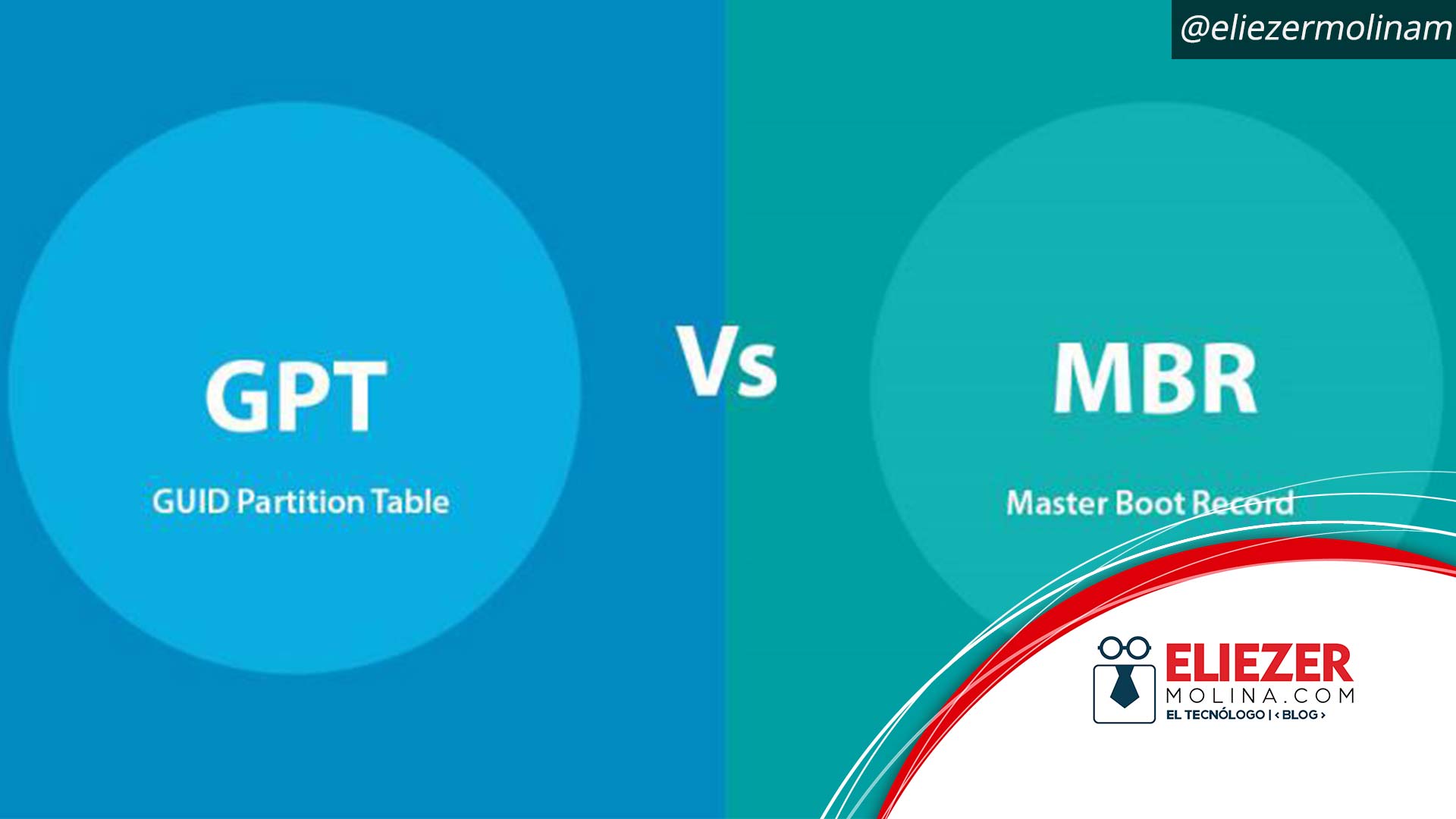
MBR vs GPT: Conoce sus diferencias
28 febrero, 2019

Robo de Identidad: ¿Qué significa y como me afectaría?
21 febrero, 2019

Cómo hacer un backup usando la consola en Windows
25 diciembre, 2018

¿Qué es y para que sirve el modelo OSI?
12 octubre, 2018

¿Qué es y para qué sirve un certificado de seguridad SSL?
10 septiembre, 2018