11 noviembre, 2024

️¿Qué es «PUM.Optional.NoChangingWallpaper» y cómo protegerte?
28 octubre, 2024

Cómo proteger a mis pastores en la era digital?
4 agosto, 2023

DHCP Snooping: Mejora la Seguridad de tu Red
28 mayo, 2023
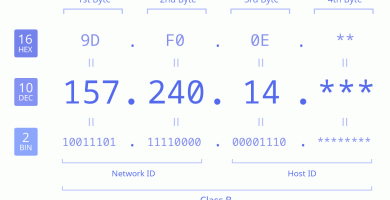
Una dirección IP pública 157.240.14.15 intenta conectar a mi red local ¿Qué hago?
15 enero, 2023

¿Cómo proteger mi identidad digital?
3 enero, 2023

¿Puede tu ISP saber lo que haces en internet?
25 marzo, 2020

¿Qué es y para qué sirve Burp Suite?
3 febrero, 2020

¿Qué es y para qué sirve Wireshark?
18 septiembre, 2019

¿Qué es y para que se un RootKit?
15 abril, 2019

¿Qué es y para qué sirve Docker?
12 octubre, 2018

¿Qué es y para qué sirve un certificado de seguridad SSL?
7 septiembre, 2018

¿Qué es un cibercriminal?
24 agosto, 2018

Organizaciones luchan con los principios básicos del ciberhigiene
9 agosto, 2018

Nuevas políticas de Google prohíben criptomineros en la Play Store
8 agosto, 2018

Las empresas sobreestiman el nivel de «confianza digital» de los consumidores
8 agosto, 2018

La detección y respuesta administradas son compatibles con los equipos de seguridad interna
3 agosto, 2018




